We all have gone through the time when we just use Facebook Login to simplify the account creation process in order to minimise the need of remembering passwords. But social login brings risks: Cambridge Analytica was found misusing user data collected by a Facebook quiz app which used the Login with Facebook feature.
In a recent report, security experts Steven Englehardt, Gunes Acar, and Arvind Narayanan from Freedom to Tinker -- a research centre that studies digital technologies in public life, have identified vulnerabilities in Facebook Login feature, wherein third party apps can track your ID, location and other demographic details.
When a user grants a website access to their social media profile, they are not only trusting that website, but also third parties embedded on that site.
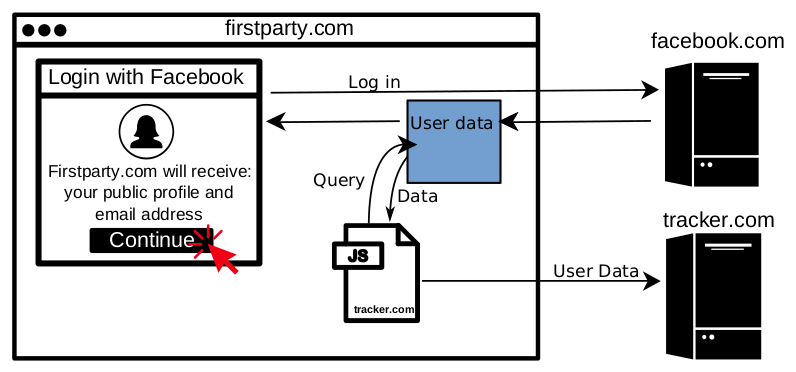
When a user clicks “Login with Facebook”, they will be prompted to allow the website they’re visiting to access some of their Facebook profile information. And even after Facebook’s recent moves to lock down the feature, websites can request the user’s email address and “public profile” (name, age range, gender, locale, and profile photo) without triggering a manual review by Facebook. Once the user allows access, any third-party Javascript embedded in the page, such as tracker.com in the figure above, can also retrieve the user’s Facebook information as if they were the first party.
The researchers found seven scripts collecting Facebook user data using the first party’s Facebook access. These scripts are found to be embedded on a total of 434 of the top one million sites. Most of them grab the user ID, and two grab additional profile information such as email and username.
The user ID collected through the Facebook API is specific to the website (or the “application” in Facebook’s terminology), which would limit the potential for cross-site tracking. But these app-scoped user IDs can be used to retrieve the global Facebook ID, user’s profile photo, and other public profile information, which can be used to identify and track users across websites and devices.
In another vulnerability, some third parties use the Facebook Login feature to authenticate users across many websites: Disqus, a commenting widget, is a popular example. However, hidden third-party trackers can also use Facebook Login to deanonymise users for targeted advertising. This is a privacy violation, as it is unexpected and users are unaware of it. But how can a hidden tracker get the user to Login with Facebook? When the same tracker is also a first party that users visit directly.
This is exactly what the researchers found Bandsintown doing. Worse, they did so in a way that allowed any malicious site to embed Bandsintown’s iframe to identify its users.
Top panel: Bandsintown’s website (represented as tracker.com) allows visitors to learn about local concerts and follow artists they might be interested in. To follow an artist, users are required to Login with Facebook and give the Bandsintown Facebook app access to their profile, city, likes, email address, and music activity. At this point Bandsintown has access to the necessary authentication tokens to access Facebook account information.
Bottom panel: Bandsintown offers an advertising service called “Amplified”, which is present on many of the top music-related sites including lyrics.com, songlyrics.com and lyricsmania.com. When a Bandsintown user browses to a website that embeds Bandsintown’s Amplified advertising product, the advertising script embeds an invisible iframe which connects to Bandsintown’s Facebook application using the authentication tokens established earlier, and grabs the user’s Facebook ID. The iframe then passes the user ID back to the embedding script.
“We discovered that the iframe injected by Bandsintown would pass the user’s information to the embedding script indiscriminately. Thus, any malicious site could have used their iframe to identify visitors. We informed Bandsintown of this vulnerability and they confirmed that it is now fixed,” the experts revealed.
Conclusion
This unintended exposure of Facebook data to third parties is not due to a bug in Facebook’s Login feature. Rather, it is due to the lack of security boundaries between the first-party and third-party scripts in today’s web. Still, there are steps Facebook and other social login providers can take to prevent abuse: API use can be audited to review how, where, and which parties are accessing social login data.
Facebook could also disallow the lookup of profile picture and global Facebook IDs by app-scoped user IDs. It might also be the right time to make Anonymous Login with Facebook available following its announcement four years ago.
